Hey ho, it’s time for some low-level shellcode encoding. After going through the encoder examples of the SLAE material i build a custom one, which you can find here.
At first i wrote a little python script which takes every single byte of a given shellcode and subtracts a random integer from it. In the end it prints the „encoded“ shellcode, its length and the used random integer.
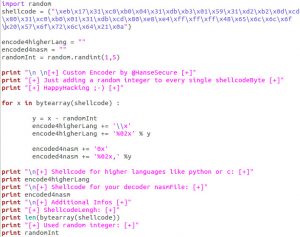 The following assembly code uses the jump-call-pop method to save the address of the shellcode into the esi register. After cleaning up the ecx register and setting up the counter (length of the encoded shellcode) the decoding process starts. The addition of the random integer to every single byte of the shellcode (stored in esi) will be done until the counter (ecx) reaches 0. Finally the execution flow jumps to the decoded shellcode.
The following assembly code uses the jump-call-pop method to save the address of the shellcode into the esi register. After cleaning up the ecx register and setting up the counter (length of the encoded shellcode) the decoding process starts. The addition of the random integer to every single byte of the shellcode (stored in esi) will be done until the counter (ecx) reaches 0. Finally the execution flow jumps to the decoded shellcode.
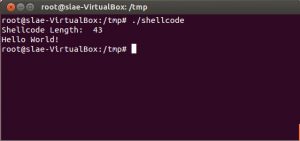
Again i just used a helloWorldPayload to demonstrate the functionality:
This encoder is not effizient, but it does his job.
This blog post has been created for completing the requirements of the SecurityTube Linux Assembly Expert certification:
http://securitytube-training.com/online-courses/securitytube-linux-assembly-expert/
Student ID: SLAE-1036