Got time to read? This tasks was a bigger one. We have to pick 3 random metasploit payloads and analyze their shellcode. After building bind and reverse shell in the first two posts i choosed the following (check all files on my github account):
- Exec whoami
- Readfile
- Adduser
Exec whoami
First I generated my shellcode via msfvenom -p linux/x86/exec cmd=whoami R | hexdump -v -e ‚“\\\x“ 1/1 „%02x“‚ and inserted it into my skeleton shellcode.c . Using gdb to analyze the behaviour in assembly. The first analyze goes through the code until the call function.
 |
|
 |
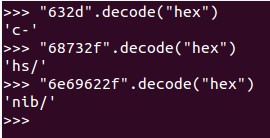
Nothing special in this codeblock, the syscall (execv) and the additional parameter are set. You can check the reverseHex stuff via your favourit language, i choose python 😉
Next the address of 0x804a05d is saved into the esp (address after call instruciton).
 The saved adress contians the string „whoami“ which is my cmd option. The rest of the code adjust the different registers for the execve command.
The saved adress contians the string „whoami“ which is my cmd option. The rest of the code adjust the different registers for the execve command.
After setting up all registers my command is executed and the username via /bin/sh -c whoami is printed to the screen.
ReadFile
Same procedure -> generating shellcode via msfvenom -p linux/x86/read_file path=/etc/passwd R | hexdump -v -e ‚“\\\x“ 1/1 „%02x“‚ and inserted into shellcode.c for the debugging process.
 |
 |
Nothing special to note. Maybe nice to see, that msfvenom also uses the jmp-call-pop instruction to save the string „/etc/passwd“ in the edx register. The garbage in the end of the assembly code isn’t important, because the last syscall (eax=0x1) exits gracefully the programm.
Adduser
Last but not least our adduser payload.
 |
 |
Until the first call instruction is executed the code seems to be ok. But then there is a lot of garbage and the inserted line for passwd is also strange, which indicates misintrepreted code. After some research via google, i found the mistake. The disassembler got a problem with the offset of the string which should be inserted into the file /etc/passwd. I have to look for a newLine in the hexCode (0A) and ignore the codeblock from the beginning of the string to the newline via msfvenom -p linux/x86/adduser -f raw | ndisasm -u -k 43,40 – .
 |
 |
Amazing, now we understand each line of our chosen payloads!
This blog post has been created for completing the requirements of the SecurityTube Linux Assembly Expert certification:
http://securitytube-training.com/online-courses/securitytube-linux-assembly-expert/
Student ID: SLAE-1036