This is just another very short usage guide for one of my little helper for pentesters and the like. During some assessments with social engineering i want to get informed by my server, if a session is opened. After some time of research i didn’t find any good solution in the internet, so i decided to write my own one 😉 Unfortunately ruby needs a GEM for TLS connections which is not in the MSF repo. My solution is a post explotation modul, which only calls my python script to send an email. You can find the code here.
0x01 Download Files
At first you should copy my repo to your favourit location via
git clone https://github.com/HanseSecure/metasploit-modules
0x02 Alter Files
Afterwards you find two files named email-notify.rb && msf-email.py .
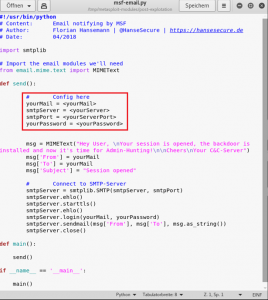
At first we have to configure our email settings for our server in the msf-email.py file.
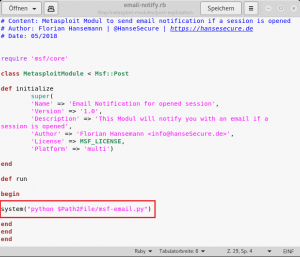
Now you have to change one line in the email-notify.rb file which should point to your altered msf-email.py file.
0x03 Copy to Position
The last step is to copy the mail-notify.rb file into your metasploit directory
cp email-notify.rb /usr/share/metasploit-framework/modules/post/multi/manage/.
0x04 Have Fun
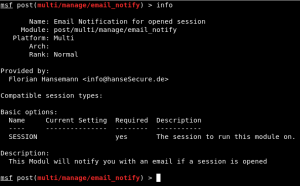
Start metasploit and look at your new post explotation tool 😉 Now you can use the set autorunscript option of your mutli/handler and the email will be send for every new session.
Cheers
Flo @HanseSecure