Why a reverse proxy is a must for your IT security
TL;DR:
Proxy servers act as intermediaries between clients and servers, improving security, optimizing performance and enabling efficient use of resources. There are two main types: forward proxies, which route outgoing traffic from clients to the Internet, and reverse proxies, which route incoming traffic from clients to backend servers.
What is a forward proxy:
A forward proxy is a server that is positioned between clients and the Internet and routes the clients’ outgoing traffic. It acts on behalf of the clients by forwarding their requests and concealing their identity. This enables the forward proxy to control Internet access, enforce security policies and improve privacy.
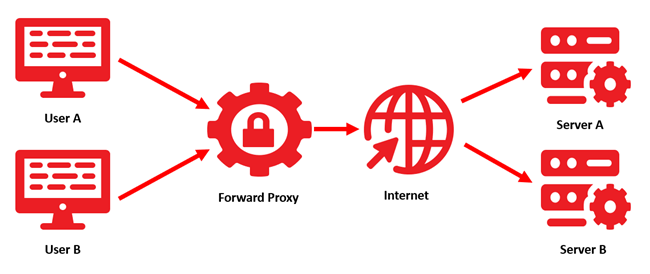
In conventional Internet communication, users (User A & User B) contact the server (Server A & B) by sending requests directly to them and receiving responses from them. However, if a forward proxy is set up, users send their requests to this proxy first instead. The forward proxy then forwards the request to the corresponding servers and receives the responses from them, which it then sends back to the users.
What is a reverse proxy
A reverse proxy is a server that is positioned in front of backend servers and forwards incoming traffic from clients to these servers. This acts as an intermediary between the clients and the backend servers, improves security, optimizes load distribution and offers functions such as SSL termination and caching.
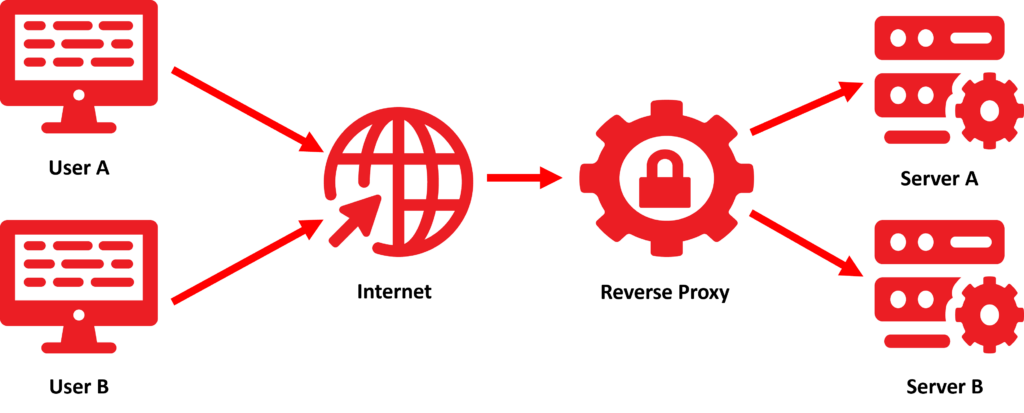
Normally, users (users A & B) communicate directly with servers (servers A & B), whereby requests are sent from the users to the servers and the servers respond directly. However, if a reverse proxy is used, all user requests go to the reverse proxy first. This forwards the requests to the servers and receives the responses. The proxy then forwards the corresponding responses back to the users.
Differences between forward and reverse proxy:
The main differences lie in their orientation and mode of operation: A forward proxy forwards traffic from the inside to the outside, while a reverse proxy directs traffic from the outside to the inside.
Forward proxies are typically used by client devices to access the Internet, while reverse proxies are often used in server infrastructures to manage incoming traffic.
Areas of application of the reverse proxy:
Basically, a reverse proxy serves as an additional security layer to ward off attacks, protect sensitive data and implement access restrictions.
- Flexibility in the authentication method
The reverse proxy enables the implementation of various authentication methods such as HTTP Basic Auth, Digest Auth, OAuth, LDAP integration, etc. Depending on the requirements of the application and the company’s security guidelines, suitable authentication methods can be selected and configured. - Locking directories
By configuring the reverse proxy, certain directories or files on the server behind the proxy can be blocked to prevent unwanted access and protect sensitive information. - IP delimitation
The reverse proxy can restrict access based on IP addresses to allow access only to certain IP ranges or trusted sources and ward off potential attackers. - SSL termination and caching
The reverse proxy can perform SSL/TLS decryption and cache frequently requested content to improve response times. - Simple configuration and scalability
The implementation of authentication at the level of the reverse proxy facilitates the configuration and scaling of the security infrastructure. Since the proxy intercepts the requests, security policies and authentication settings can be managed centrally and applied to all incoming requests, regardless of the underlying servers. - Protection against attacks and misuse
The reverse proxy protects the backend servers from brute force attacks, unauthorized access and other forms of misuse. Security can be further increased by using captchas, two-factor authentication and other security mechanisms. - Load balancing
Some reverse proxies can also act as load balancers and distribute the data traffic across several servers. This can ensure that no single server is overloaded and that user requests can be processed without delay.
Why it is worthwhile for your company:
- Your company benefits from the improved security, performance and scalability offered by a reverse proxy.
- They can use their server resources more efficiently, fend off attacks and improve the user experience.
- By implementing a reverse proxy, companies can raise their IT security standards and thus also increase customer satisfaction.
We support you at all times during implementation.
Outlook:
In our next blog post, we will explain how you can set up your own reverse proxy server easily and free of charge. You must not miss this!



