Blog
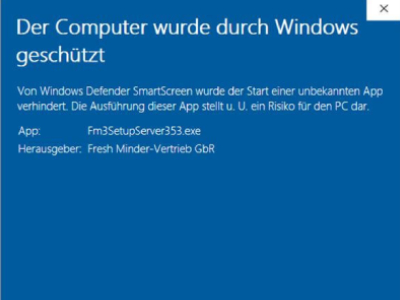
During my last assessment, I noticed some strange behavior with Microsoft’s SmartScreen feature. Basically, this security feature should block the [...]
7. July 2019
Description Screenshots of applications that are moved to the background are created for better user experience. Unfortunately, other apps can [...]
1. July 2019
I decided to set up a new team of infosec professionals, because of a lot of project requests and my [...]
25. October 2018
CVE CVE-2018-7272 Vulnerable software AM 5.0.0, 5.1.0 Vulnerability Unauthorized access Timeline 15.12.2017 Seller informs X.01.2018 Manufacturer has patched vulnerability 24.01.2018 Manufacturer [...]
25. August 2018
CVE CVE-2018-16231 Vulnerable software FTP server <= 8.4f Vulnerability Remote denial of service Timeline 30.01.2018 Seller informed(also local BO ) [...]
25. August 2018
Welcome to my next blog post. Today I want to show you some basic pentesting stuff. We will manually backdooring [...]
19. June 2018
From 21.11. The SECUTA Information Security Conference will take place in Garmisch-Partenkirchen from November 1 to 23, 2018. There, the [...]
18. May 2018
This is just another very short usage guide for one of my little helper for pentesters and the like. During [...]
30. April 2018
This is a short usage guide which should explain my simple wrapper for the spike fuzzer, which you can find [...]
6. March 2018
Vulnerable software FTP server 8.0f(g) Vulnerability Local Buffer Overflow (SEH protected)-> Code Execution Time Line 01/24/2018 Vendor informed 01/30/2018 [...]