Blog
As promised on Twitter here is my OSCE review. You can read my time line from before course enrolling until [...]
20. February 2018
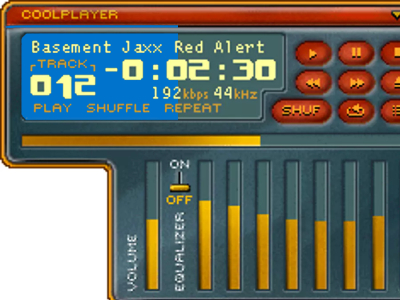
While doing my preperation for the OSCE i found an exploit for the coolpalyer+ version 2.19.1 from 2009. I decided to [...]
19. February 2018
On 27.02.2018 between 1 and 4 p.m., the Munich Chamber of Commerce and Industry is offering a roundtable discussion for [...]
7. February 2018
The tiresome topic of passwords and their management. I am always asked how to solve this problem. Therefore, I decided [...]
8. January 2018
The last post for my SLAE certification is about encryption of shellcode. As usual you can find all my files [...]
23. November 2017
This task (pick up 3 shellcodes from Shell-Storm and use polymorphism to beat pattern matching) sounds really sophisticated but you [...]
10. October 2017
Got time to read? This tasks was a bigger one. We have to pick 3 random metasploit payloads and analyze [...]
9. October 2017
Hey ho, it’s time for some low-level shellcode encoding. After going through the encoder examples of the SLAE material I [...]
9. October 2017
Ready for the next level? – Method to exploit software even with small space for shellcode: EggHunting The third task [...]
9. October 2017
Welcome back to my second post for the SLAE certification. Today we are going to build a reverse_shell shellcode and [...]