During my last assessment, I noticed some strange behavior with Microsoft’s SmartScreen feature.
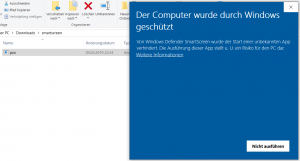
Basically, this security feature should block the execution of untrusted files from the Internet(more information).
In fact, the execution of untrusted applications is blocked when trying to open them via the GUI(file explorer).
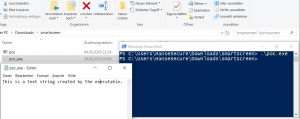
However, the execution is not blocked when opening the application via a command line tool like cmd or powershell xD
I have already tweeted about this behavior and Matt had a logical response for this behavior.
Still, I find this behavior funny and think that most admins don’t know this. That’s why I decided to write this short post.