New InfoSec Team spawned: BreachedSec
I decided to set up a new team of infosec professionals, because of a lot of project requests and my limited time. This team consists of people, who got a deep passion about pentesting and redteaming. Every team member will be presented at the page and the clients will always know who is in charge. […]
CVE-2018-7272: AM 5.0.0, 5.1.0

CVE CVE-2018-7272 Vulnerable software AT 5.0.0, 5.1.0 Vulnerability Unauthorized access Timeline 15.12.2017 Seller informs X.01.2018 Manufacturer has patched vulnerability 24.01.2018 Manufacturer publishes safety notice Description Forgerock ‘s AM is vulnerable to unauthorized access. TokenIDs are sent via HTTP GET requests that are stored in various places, such as proxy logs, local browsing history, and the like. This could […]
CVE-2018-16231: Remote DoS in Personal FTP Server <= 8.4f

CVE CVE-2018-16231 Vulnerable software FTP server <= 8.4f Vulnerability Remote denial of service Timeline 30.01.2018 Seller informed(also local BO ) X.02.2018 Vendor patched vulnerability local BO 31.07.2018 Seller informed again 31.08.2018 Disclosure Description Michael Roth Software Personal FTP Server (PFTP) up to 8.4f allows remote attackers to cause a denial of service (daemon crash) by […]
Backdooring PE-File (with ASLR)
Welcome to my next blog post. Today I want to show you some basic pentesting stuff. We will manually backdooring a PE file, in this case the putty client. I used the following software setup: Windows 10 Pro 32 bit Putty Stud_PE Immunity debugger Before we are getting our hands into assembly, i want to […]
HanseSecure at IT-Secuta 2018

From 21.11. The SECUTA Information Security Conference will take place in Garmisch-Partenkirchen from November 1 to 23, 2018. There, the current developments and challenges of information security will be shown in a practical way and solutions will be presented. The program includes live sessions, live hacking, current IT case law and the topic of EU […]
HowTo: MSF email

This is just another very short usage guide for one of my little helper for pentesters and the like. During some assessments with social engineering i want to get informed by my server, if a session is opened. After some time of research i didn’t find any good solution in the internet, so i decided […]
HowTo: ExploitDev Fuzzing

This is a short usage guide which should explain my simple wrapper for the spike fuzzer, which you can find here. For this example i used the well known vulnserver 😉 0x01 Determine possible commands A simple nc && HELP command revealing all possible commands. 0x02 Create Text File containing commands Just Copy&Paste 😉 0x03 Fire […]
Vulnerability: Local Buffer Overflow in Personal FTP Server 8.0f(g)
Vulnerable software FTP server 8.0f(g) Vulnerability Local Buffer Overflow (SEH protected)-> Code Execution Time Line 01/24/2018 Vendor informed 01/30/2018 Vendor reminded 12.02.2018 Software patched 20.02.2018 Vulnerability Disclose Description The free FTP Server from Michael Roth Software is vulnerable to a local buffer overflow. One of the advanced options within the application didn’t have input […]
Offensive Security Certified Expert && me
As promised on Twitter here is my OSCE review. You can read my time line from before course enrolling until the end of the exam here. So, let’s go. Stage_0: Preparation just before enrolling! First, I read a ton of other reviews to get an idea about the course and the exam. There is nothing […]
CVE-2009-1437: RCE in CoolPlayer+ <= 2.19.6 (Windows 10 Pro)
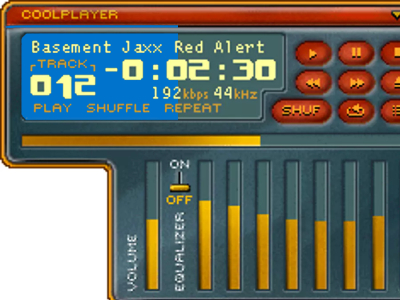
While doing my preperation for the OSCE i found an exploit for the coolpalyer+ version 2.19.1 from 2009. I decided to check this vulnerability in the recent software version (2.19.6) on my Windows 10 machine. The following post descripes the exploit development. 1. create PoC I created a small python script, which creates a .m3u file […]
