While doing my preperation for the OSCE i found an exploit for the coolpalyer+ version 2.19.1 from 2009.
I decided to check this vulnerability in the recent software version (2.19.6) on my Windows 10 machine. The following post descripes the exploit development.
1. create PoC
I created a small python script, which creates a .m3u file with 5000 “A” characters.
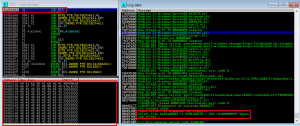
After attaching the program to a debugger and loading the file into the coolplayer, it crashed. The EIP and some registers are overwritten with my characters -> The vulnerability still exists.
2. determine the offsets
For the next step i created a pattern via
pattern_create -l 5000
replaced the “A” characters with it and checked the offsets in immunity debugger with mona via
!mona findmsp
To check this result i changed my exploit script and reload the new file into the coolplayer.
The EIP is overwritten with my “B” in hexformat \x42.
3. looking for jumps into my code cave
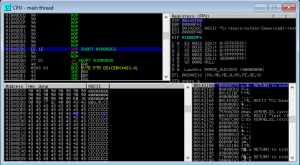
I examined the space for the registers and noticed that the ebx register would be a perfect place to jump. Using mona i found a suitable address via
!mona jmp -r ebx
I converted the address in reverse hex format and replaced my four “B “s with it.
Loading my new “malicious” file and setting a breakpoint at the call ebx function leading to my capital “A” buffer.
4. checking the possible space
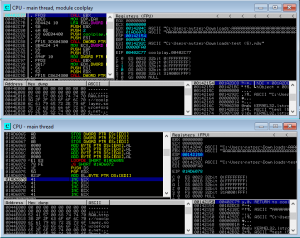
Now i checked the possible space for my shellcode in ebx.
Just 240 bytes -> Too small for a payload such as a reverse shell. I noticed my buffer of capital “C” after some instruction in the end of my first buffer. So I decided to take a short jmp at the end of my first buffer.
5. final exploit
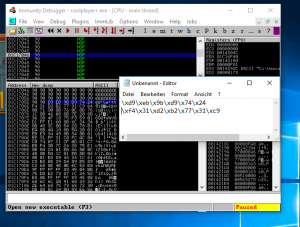
Finally i used a nop sled and placed my shellcode (starting with \xd9\xeb\x9b\xd9\x74\x24).
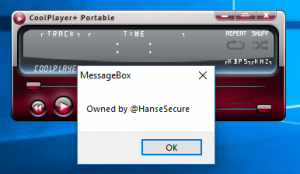
And Code Execution !
You can find the final exploit here.