From AWAE to OSWE: The Preperation Guide

As promised on Twitter this post will document my steps through the OSWE exam preperation. Searching for available study material After some google action i found some useful stuff Step 1: The Plan I decided to follow the training order mentioned in AWAE-PREP because it seemed logical considering the AWAE course material. Step 2: Start […]
Best Practice: Intel Unquoted Service Path

Affected Software Intel Management Interface <= 1815.12.0.2021 Issue In my last assessment I discovered an unquoted service path in the Intel Management Engine Interface. In general this could lead to privilege escalation on a system, if the service is running with higher privileges and we (unprivileged user) got writing permissions along the installation path of […]
HanseSecure as one of the top 21 – twice

It’s funny that two independent companies name the “21” cybersecurity and redteaming resources in the world. But I appreciate being named in both lists. One is an American tech blog called Techbeacon and the other is the American endpointprotectoin company SentinelOne. 2018 – Techbeacon: Modern Red Teaming: 21 resources for your security team. https://techbeacon.com/security/modern-red-teaming-21-resources-your-security-team 2019 […]
CVE-2019-12763: Insecure data storage security camera CZ

CVE CVE-2019-12763 Vulnerable software Android App: Security Camera CZ <= 1.6.8 Vulnerability Insecure data storage(M2, OWASP Mobile Top 10, 2016). Timeline Description The Security Camera CZ application up to 1.6.8 saves images of the recorded videos to the external data storage. These images could contain very sensitive and personal data, as they are often used […]
SmartScreen Bypass = strange?
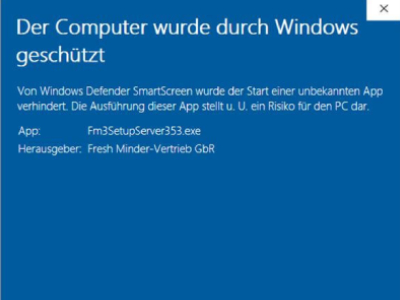
During my last assessment, I noticed some strange behavior with Microsoft’s SmartScreen feature. Basically, this security feature should block the execution of untrusted files from the Internet(more information). In fact, the execution of untrusted applications is blocked when trying to open them via the GUI(file explorer). However, the execution is not blocked when opening the […]
HMV-01: Automatically generated screenshots
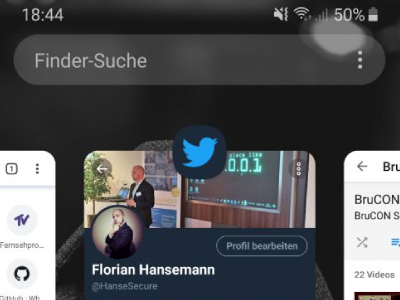
Description Screenshots of applications that are moved to the background are created for better user experience. Unfortunately, other apps can access them, exposing sensitive data such as banking information, passwords, or personal information. Example All applications in the background can be viewed (screen shots). Countermeasures Use the FLAG_SECURE to hide the screen when an app […]
