
In the past few weeks, I have created a number of webinars and documents that can help companies and possibly also one or two private individuals to protect themselves in the home office. Depending on how much time you can/want to spend for this, you just have to choose the right paragraph 😉
For those without time
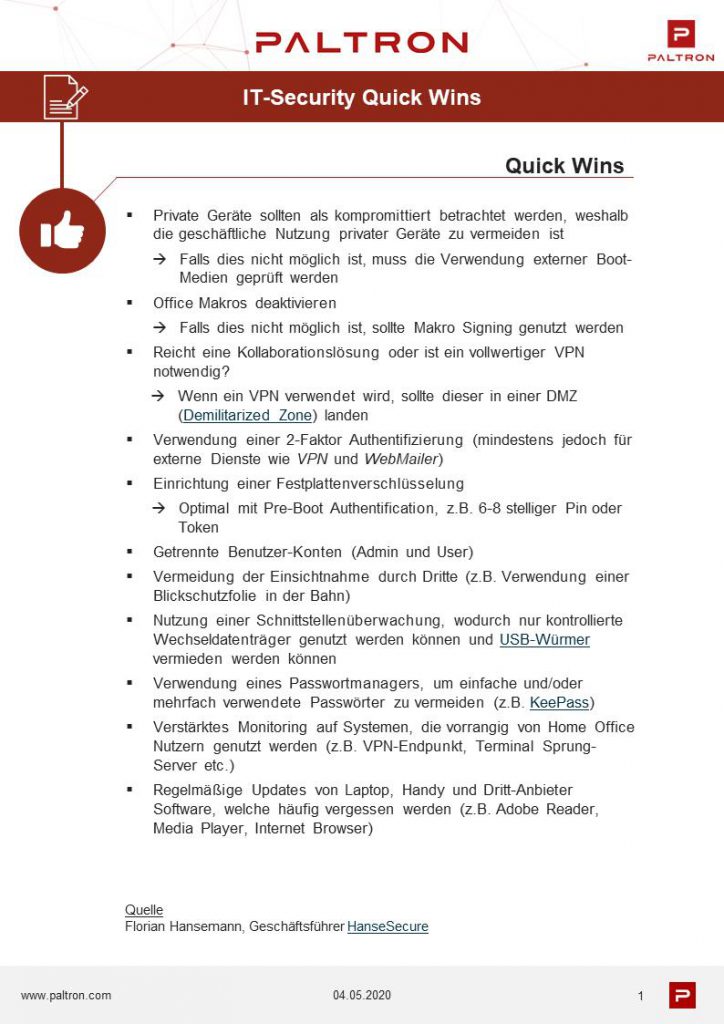
QuickWins: Simple measures with great effect
(I will deliver the PDF version later)
First publication on 08.05.2020 on LinkedIn
For those with a little more time
Slides of my webinar “IT-Security in the HomeOffice” at the IHK Munich
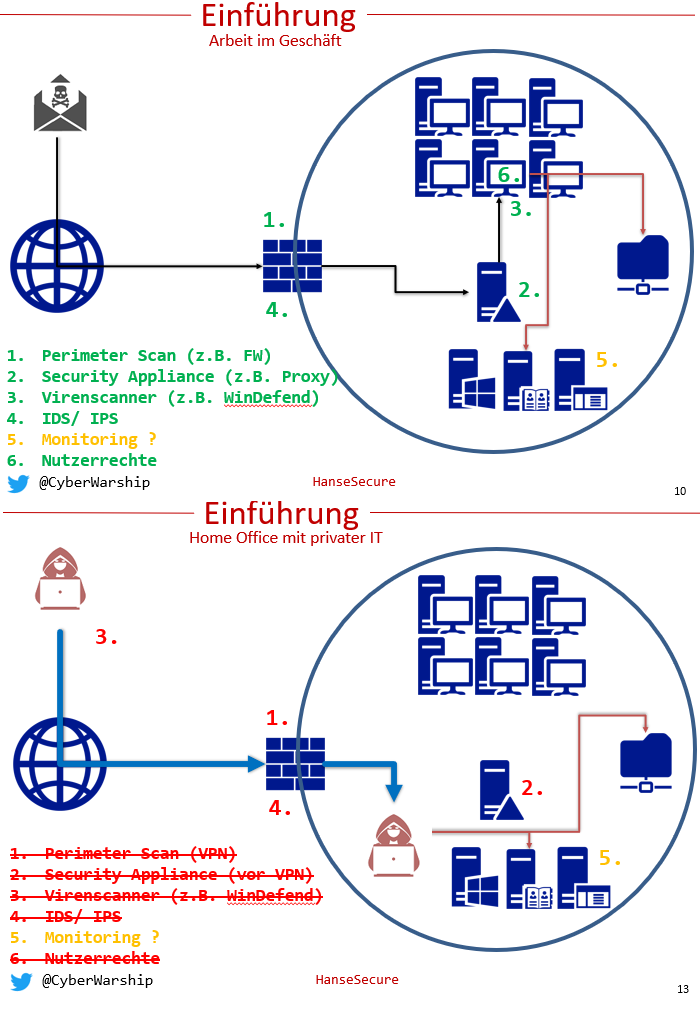
First, there is a short introduction to the topic HomeOffice, respectively I show the essential differences with regard to security measures.
I then go into the typical attack vectors on users in the HomeOffice. I then outline the potential impact of a compromised client on your network. At the end I show different ways to make it harder for the attacker 😉
First publication at the IHK Munich on 06.05.2020 (search for Hansemann 😉
For those with a lot of time
Recording of my webinar “IT Security in the HomeOffice” at the IHK Munich.
Timeline:
- 00:00 – 06:00 Greeting
- 06:00 – 09:00 Information about myself
- 09:00 – 11:00 General introduction
- 11:00 – 17:30 What protection mechanisms does an attacker have to overcome in the “ideal” corporate network?
- 17:30 – 19:30 What protective mechanisms does an attacker have to overcome in the home office?
- 19:30 – 21:00 What protective mechanisms must an attacker overcome in the home office with private IT?
- 21:00 – 30:45 Questions from the floor
- 30:45 – 34:45 How are users attacked in the HomeOffice?
- 34:45 – 37:00 Effects of a compromised computer
- 37:00 – 52:00 Simple measure with great effect for more IT security
- 52:00 – 54:10 Idea to protect private IT (if there is no other way).
- 54:10 – 54:18 Overview of all measures
- 54:18 – 72:00 Questions from the floor
- 72:00 – * End
Conclusion
Have fun reading / looking and setting up 😉
Questions and criticism gladly via Twitter or email.
PS:
Whoever liked/helped is welcome to leave me a review on Google.



