#2 Domain admins everywhere
The attack
It is a Monday morning and Kevin Vielzutun starts his monthly server check in the network, because he is one of 3 administrators of Fahrlässig GmbH with about 100 employees. To save time and thus work more efficiently, Kevin performs these checks as usual with his Domain Admin account, otherwise he would have to log in multiple times with different accounts.
However, on his computer he still has so many remote desktop windows open from yesterday that he can’t find the right one 🙁
Therefore, he starts a new session on his server Tray1 to find that another domain admin account is already logged in here. This problem occurs more often because his colleague Otto Mirdochegal also frequently forgets to end his remote sessions. This was also the case for the next 3 systems, so Kevin got tired of his server checks and decided to do something else first.
Now Keven wanted to take care of the ticket of Mr. Lustig, who had a problem with macros on an Excel sheet of SuperSchnell GmbH last week.
While trying to reach Mr. Lustig, he still wonders why Otto is logged on to his server with the ancient ITADMIN (Domain Admin) account. Because Otto is on vacation, has never been on this server and he did not know the account ITADMIN… Well, Kevin can ask that when Otto comes back from vacation next week….
What happened?
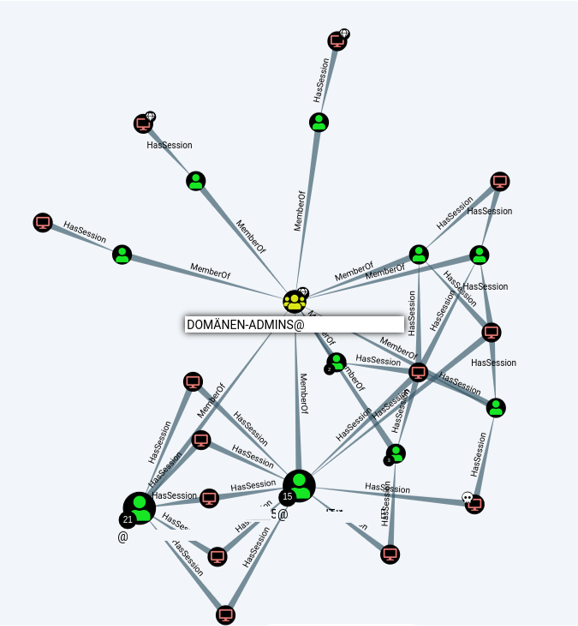
After Mr. Lustig ran the macro on his computer last, an attacker had gained control of his system. Subsequently, the latter looked around the network to maximize its rights in the network. Here it was very quickly apparent that, despite the small size of the company, numerous domain admin accounts existed and these were logged on to “normal” clients & servers.

During the evaluation it became clear that the 3 admins in house, created about 20 accounts with domain admin rights and with these on almost half of the systems in the company did not log off. Now the attacker had a choice of over 50 systems where he could pick the most vulnerable one to compromise and then take over the domain admin’s session.
The countermeasure
Basically, there are two ways to demand more from the attacker and to protect yourself better:
Domain Admins only on Domain Controller
These two terms/ AD objects not only sound similar, but are equally important for any network with a Windows domain. Domain administrators must never connect to other servers or even clients, as they can usually be compromised much faster than a domain controller.
Number of Domain Admins
There should be no more than 2-3 Domain Admins in a network and they should be designated exclusively for activities on the Domain Controller (e.g. configuring GPO).
For all other activities (support, software installation, server configuration, virus scanner or incident response xD …) dedicated groups should be created, which can only be used for the specific tasks.
Safety gain
High
*From the blog series Top Security QuickFails