Blog
E-Mails gehören nach wie vor zu den wichtigsten Kommunikationsmitteln – sowohl im privaten als auch im geschäftlichen Umfeld. Gleichzeitig sind [...]
9. October 2025
As already explained in our article on proxies, there are many reasons for using a reverse proxy. But how do [...]
12. November 2024
As promised on Twitter this post will document my steps through the OSWE exam preperation. Searching for available study material [...]
5. August 2019
Welcome to my next blog post. Today I want to show you some basic pentesting stuff. We will manually backdooring [...]
19. June 2018
This is just another very short usage guide for one of my little helper for pentesters and the like. During [...]
30. April 2018
This is a short usage guide which should explain my simple wrapper for the spike fuzzer, which you can find [...]
6. March 2018
As promised on Twitter here is my OSCE review. You can read my time line from before course enrolling until [...]
20. February 2018
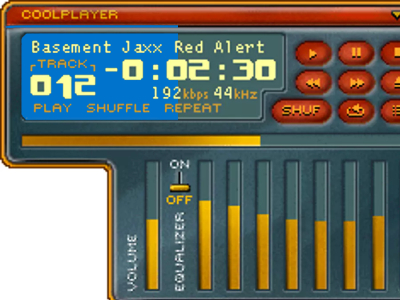
While doing my preperation for the OSCE i found an exploit for the coolpalyer+ version 2.19.1 from 2009. I decided to [...]
19. February 2018
The last post for my SLAE certification is about encryption of shellcode. As usual you can find all my files [...]
23. November 2017
This task (pick up 3 shellcodes from Shell-Storm and use polymorphism to beat pattern matching) sounds really sophisticated but you [...]