Upcoming blu Systems Praxistalk with Florian Hansemann
On 21.07.2022 it’s that time again. Our founder and IT security specialist Florian Hansemann will be a speaker at the blu Systems Praxistalk 2022 in Munich around the topic “Security simple, fast and free of charge.” Speak. This year’s blue Systems Praxistalk will take place under the overall theme “Digital Governance – Just Another Buzzword?”. […]
Attention rip-off: HanseSecure on Kabel 1
Ihm seien verdächtige Überweisungen aufgefallen. Er fragt, ob er sie stoppen soll. Sie bejahen es und geben zur Identifikation Ihrer Identität eine TAN durch. In diesem Moment schnappt die Falle zu. Unser IT-Sicherheitsexperte Florian Hansemann hat vor Kurzem bei einem Kabel 1 Beitrag rund um das Thema Phishing und Social Engineering mitgewirkt. In diesem Beitrag […]
HanseSecure recognized as one of the Top 100 Cybersecurity Leaders

Cybersecurity is a topic that is gaining more and more attention, with over 80,000 cyberattacks reported every day. In Germany alone, at least 92% of companies report that they have been affected by some type of cyberattack within a 12-month period. Fortunately, cybersecurity companies are constantly expanding their offerings to businesses and corporations to improve […]
HanseSecureCar #1

Introduction In the next few weeks you will be able to follow how the first HanseSecure company car was selected, purchased and “customized”. The whole process was extremely exciting and thrilling for me personally because A comparatively large investment So far there was nothing big besides my laptop and […]
IBM Talk, the first

Our managing director Florian Hansemann was allowed to participate in a Christmas special at the IBM headquarters on 07.12.2021. All presentations revolved around the topic of SOC & SIEM or QRadar. Only our presentation stood out a little bit, as we were the only speech teamer who was allowed to look at the other […]
First radio post: Fake vaccination cards

On 02.11.2021 I was allowed to give a short contribution with the German wave to the topic of the falsified vaccination cards. Due to the fact that the topic took place very extensively in the Eastern European region, only the Russian-speaking section of the station dealt with the topic. So do not be surprised that […]
Top Security QuickFails: #5 Attack of the CloneAdmins aka Missing LAPS

#5 Attack of the CloneAdmins aka Missing LAPS The attack At FaulerHund AG in Munich, the employees are starting a new business year and are looking forward to new challenges. So also the administrator Karl KannNixDafür, who noticed on Thursday noon around 12:30 that the account of Ute Unbeschwert is still logged in, although she […]
Top Security QuickFails: #4 No SPF

Half past six in the morning in Germany. Bianca at MedienBude GmbH starts her workday by checking her e-mail inbox.
There you will find an urgent email from your boss asking you to check the last statement.
Top Security QuickFails: #3 The “invisible” network shares

#3 The “invisible” network shares The attack It’s Wednesday morning, the sun is shining and all ImmerGrün AG employees are looking forward to the summer party in the afternoon.Beate from the HR department wanted to have a look at some applications from the previous day and was surprised that many documents suddenly required macros to […]
Top Security QuickFails: #2 Domain Admins Everywhere
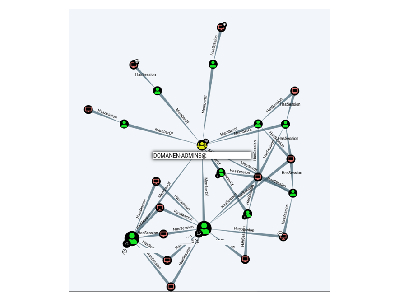
#2 Domain admins everywhere The attack It is a Monday morning and Kevin Vielzutun starts his monthly server check in the network, because he is one of 3 administrators of Fahrlässig GmbH with about 100 employees. To save time and thus work more efficiently, Kevin performs these checks as usual with his Domain Admin account, […]
