Mastering Security: Wie nutze ich Vaultwarden?

In einem unserer letzten Blogposts haben wir bereits vorgestellt, wie man die Open Source Version des bekannten Passwortmanagers Bitwarden installiert. In dem heutigen Beitrag erklären wir nun, wie man diesen verwendet. Die folgenden Begriffe werden dabei häufiger genannt werden: 1.1 Erstellung eines neuen Passworts Wenn wir ein neues Passwort speichern wollen oder ein neues Passwort […]
IT emergency card
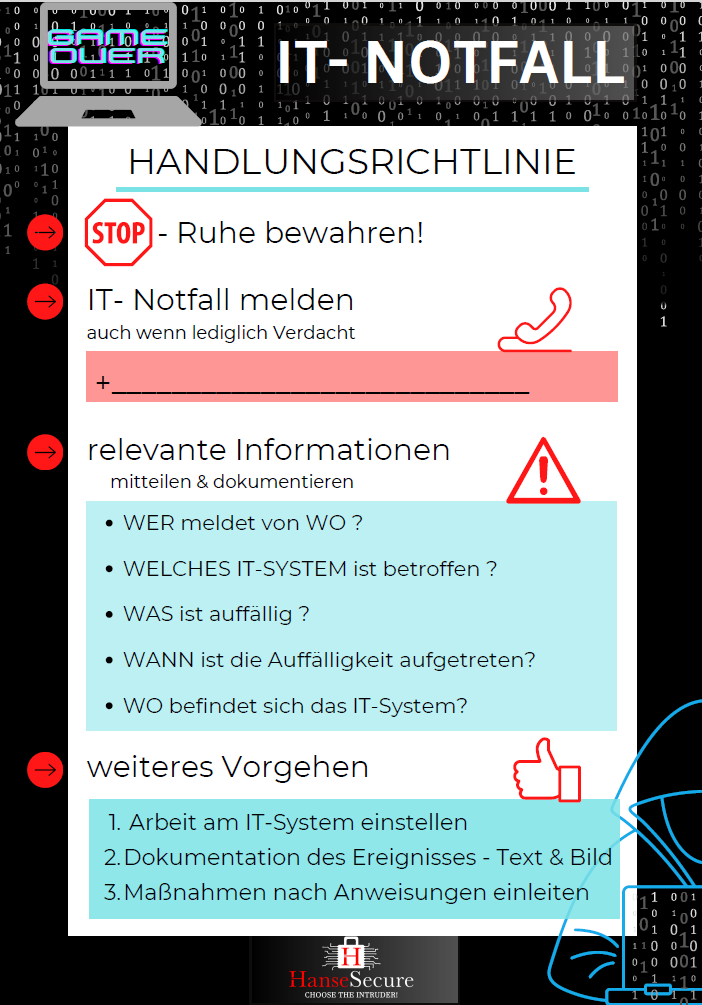
An emergency and what to do now? Emergency cards give us a guideline in uncertain or critical situations. HanseSecure’s IT EMERGENCY CARD provides all users with compact instructions for action. In addition, the company’s security awareness is also increased significantly. By acting with guidance, they experience security and protect themselves and others directly from further […]
The role of the CISO in modern corporate security

At a time when digital threats and cyber attacks are on the rise, the role of the Chief Information Security Officer (CISO) in companies is becoming increasingly important. But what exactly does a CISO do, and why is their position so crucial to a company’s security? The importance of the CISO The CISO is the […]
The alarming increase in cyber attacks: Why every business is at risk

Cyber attacks are no longer just a problem for large companies or organizations in the public eye. Medium-sized companies and seemingly insignificant industries are also increasingly being targeted by cyber criminals. The latest figures show an alarming increase in attacks on companies of all sizes and industries. No company is too small or too insignificant […]
Proxies: The invisible helpers of Internet traffic
Proxy servers act as intermediaries between clients and servers, improving security, optimizing performance and enabling efficient use of resources. There are two main types: forward proxies, which route outgoing traffic from clients to the Internet, and reverse proxies, which route incoming traffic from clients to backend servers.
Mastering Security: The benefits of a password manager and how you can create your own
In an increasingly digitalized world, where our personal and professional information is often stored online, the security of our passwords is crucial. Using a password manager is not only a practical but also an extremely important measure from a security perspective. In this blog post, we will look at the reasons for using a password […]
Visit us at the IT security trade fair ITSA – Stand 7-239!

Enter your headline here We have exciting news for you! We will be at the IT security trade fair ITSA this year and would be pleased to welcome you at our booth 7-239 from October 10 to 12, 2023. There we will show you the latest developments and solutions in the field of IT security. […]
SMS scams: How you can protect yourself from the most common messenger scams
Protect yourself from messenger scams. Find out how you can protect yourself from scams such as the “parent trick” or fake customer text messages.
The dark side of AI – How ChatGPT is becoming a tool for cybercrime

Florian Hansemann, cyber security expert, reveals: How ChatGPT is becoming a weapon in cybercrime and why AI regulation is important now.
HanseSecure at the Walkshow: Cyber. For sure!

Expert talk by TÜV SÜD Academy A joint walk and maximum input – that’s what characterizes the TÜV SÜD Academy walk show.Florian Hansemann was invited as a security expert and presented concrete options for action for private individuals and companies. Social engineering is something we encounter daily and at scale. Data from private individuals has […]
